Social Engineering in Mass Medias : The Case of Enigma Software Group
By Adam Richard, Information Security Consultant
Introduction
The story behind this whole article began a few months ago, on June 25th 2010 to be precise, when I read a news article on the web that had been submitted to me by one of the few security mailing lists that I'm subscribed to. The article was actually about a so-called demographic study revealing an apparent higher infection rate in Southern cities of United States compared to the North of the country ("Southern Cities Have High Malware Rates" : http://threatpost.com/en_us/blogs/southern-cities-have-high-malware-infection-rates-062510?utm_source=Newsletter_062510&utm_medium=Email+Marketing&utm_campaign=Newsletter&CID= ). This article mentions an online malware-tracker world map that keeps track in real time about malware infections and report them by geographical location (http://www.enigmasoftware.com/). Even though the data presented is only very partial because it comes from a single source, this site immediately got my interest as it provided me with a few stats linked to the rural remote area in which I now live in. Being required to provide such localized statistics for my business case for the small consulting firm I want to start down here in order to convince my funds providers of the relevancy of my business in the economical landscape of the region (as apparently they felt apart from the rest of the Internet), I was just too happy at my finding to listen to all the small alarm bells that tingled in my mind, much like Spider-Man's spider-sense when I reviewed the website in question more in depth. I wanted to contact the company who owned this website Enigma Software Group (ESG) about some inquiry, but not finding any e-mail address (my favorite means of communication) on any of their page, I simply gave up about it and forgot the thought.
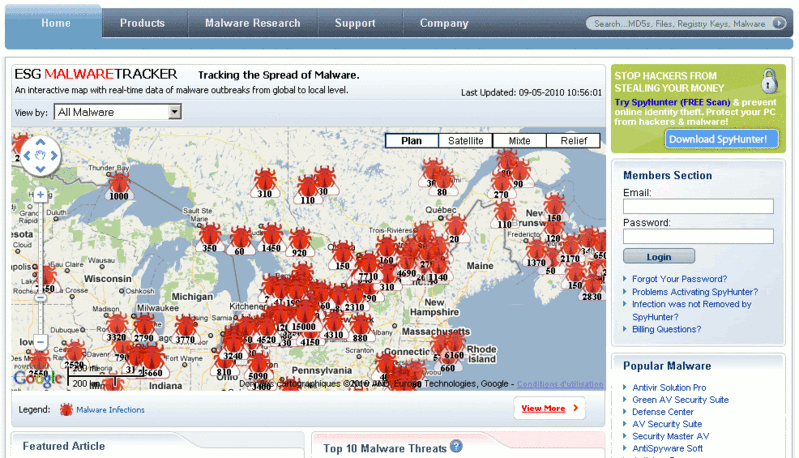
Figure 1. ESG's Malware Tracker Map
Until about a month later, at which time I was shockingly surprised to see the infection rates in small cities in my area go up by nearly 300%. Thinking that this was adding weight to my business case (and in a sense it did), I took more time to scrutinize the tracker software's methodology, in order to get as much meaning out of the numbers as possible. For example, there was a discrepancy on the malware-tracker site that I found hard to explain to my creditors so that they couldn't just brush off this data as being invalid or of unreliable source. Not that they could have found that out by themselves, but like many security enthusiasts, I'm a little paranoid with details and have a tendency to be a perfectionist at times, often expecting for the worse to happen and plan accordingly. With that being said, the discrepancy in question was about the fact that the site reported stats for relatively small-sized towns, along with the biggest city of the province I live in, Montréal. But it showed no stats for Québec City, which is the second most important city of the province, along with its Capital. Zooming out of the map, I finally found what was wrong when I saw an incredibly large number of reported infections out in the middle of nowhere, in the northern part of the province of Québec.
And that's when I found out what the problem with the discrepancy was : the stats for Québec City were tagged with the "Québec" label meant for the province as a whole (and which appears first in the site's parser), rather than to the "Québec" label meant for Québec City. As a helping gesture, I decided to contact them about it so that they could fix this minor flaw on the display system of what I otherwise thought of being a really cool tool. So, I tried to look for a e-mail contact somewhere... ANYWHERE on the company's website, and couldn't find anything resembling it, without actually shelving out a few bucks to register their scanner software from which the stats were based upon which would then grant me access to e-mailing a support technician.
And that's when my spider-sense began tingling again. And this time, I really took the time to look into it.

Figure 2. I need to pay money to tell them about a broken piece on their website? I think not.
In the light of my findings, and considering that this originally came to me as a reliable piece of security news provided from a generally trusted source (the Threatpost mailing list backed-up by Kaspersky Labs) the idea came to me to investigate the depth of the media coverage ESG received in recent years, and how they apparently managed to make a virgin image of themselves despite a shady and rocky past. As for the present, the company claims as hard as it can that it is now operating legitimately, and even threatened to take legal action against anyone pretending to the contrary, so I'll content myself with just reporting the facts the way I see them and let you, the reader, be the judge. The result of my investigation is presented in this article, and sheds some interesting lights about what I can only describe as social engineering techniques aimed at the mass medias (as opposed to a single person or small group of people) in an attempt to not only regain a certain level of apparent virginity, but also as a means to boost sales of a product of which the quality of is still matter to debate.
As a disclaimer, since there will be question of credibility a lot throughout this article, I feel that it is only fair that I provide some background info about myself. So, for the record, I got my first computer at age 12, a Commodore 64, and learned programming on that box. I later went to University, then worked as a technical support person for a couple of large companies for a few years. Then in 2000, following a burn-out, I became a self-learner security enthusiast, writing a few technical research articles and pioneering in the log management department with Open Source softwares (LogAgent, LogIDS, LogMonitor, ComLog, SIDTk) what unfortunately (for me) never got quite the buzz and support that Snort did at the time. This material has been presented in the academical conference Seguridad en Computo in Mexico City over the years of 2000-2004, in which time-frame I worked for two security companies (one of them based in Paris, France) and tried to sell a commercial version of my Open Source softwares, which never really panned out. I also did a conference in Québec City, and got invited at the Canadian Embassy in Washington as part of a government-backed IT security economical mission in the US, all in 2004. I took a break completely from computer security in 2005, and at 37 now, seeing how things have so little changed and not feeling one bit out of the loop due to my 5-years non-exposure, I am attempting my way back into it in my small-town, French-speaking birthplace. One of my softwares, ComLog has been falsely flagged as malware in the past, and may still be today, which means that I am fully aware of what it is to be put into ESG's situation. The irony of it being that it my case, ComLog is labeled as a keylogger spyware, when in fact it was designed from an admin's perspective in order to provide him with a history of commands that a hacker could be passing through cmd.exe (as this was a popular trend when IIS4 directory traversal attacks were the norm), and thus allowing him to know exactly what happened over the course of an attack, and take proper immediate action (when combined with LogAgent to centralize in real-time the logged info). A subtlety that some "anti-malware" vendors of the time, trying to build up a reputation by buffing up the number of actual "threats" detected as much as possible as a way to build street-cred, failed to see, despite my explanations to them. But I digress.
So, enough about me, and hang on to your seats folks, as you risk falling down your chair on more than one occasion as you discover some of the amazing stuff missed by the reporters of major media outlets such as CNN.com, NBC, USA Today, CNET, Information Week (http://www.enigmasoftware.com/about-us/esg-in-the-news/) and even security-aware mailing lists like Threatpost (who politely declined to follow-up on this issue) among many others, and which just proves how just about anyone can use today's "journalism laziness" to their advantage to social-engineering them into doing their own marketing campaigns for them for free, and for a product of dubious reputation thanks to its long history (ESG's SpyHunter has been around 1999), no matter what is ESG's stand on the state of its product nowadays. Some of these things are so big that it becomes obvious that any and all journalist, reporter and media outlet that jumped into the ESG bandwagon didn't do the simplest of background check on Enigma Software Group and its spokespersons and took their words for face value. Once you put together the findings gathered over about 60 websites (reached through very simple Google searches), it quickly becomes clear that ESG's credibility isn't on par with what they claim to be.
Figure 1. ESG's Malware Tracker Map
Until about a month later, at which time I was shockingly surprised to see the infection rates in small cities in my area go up by nearly 300%. Thinking that this was adding weight to my business case (and in a sense it did), I took more time to scrutinize the tracker software's methodology, in order to get as much meaning out of the numbers as possible. For example, there was a discrepancy on the malware-tracker site that I found hard to explain to my creditors so that they couldn't just brush off this data as being invalid or of unreliable source. Not that they could have found that out by themselves, but like many security enthusiasts, I'm a little paranoid with details and have a tendency to be a perfectionist at times, often expecting for the worse to happen and plan accordingly. With that being said, the discrepancy in question was about the fact that the site reported stats for relatively small-sized towns, along with the biggest city of the province I live in, Montréal. But it showed no stats for Québec City, which is the second most important city of the province, along with its Capital. Zooming out of the map, I finally found what was wrong when I saw an incredibly large number of reported infections out in the middle of nowhere, in the northern part of the province of Québec.
And that's when I found out what the problem with the discrepancy was : the stats for Québec City were tagged with the "Québec" label meant for the province as a whole (and which appears first in the site's parser), rather than to the "Québec" label meant for Québec City. As a helping gesture, I decided to contact them about it so that they could fix this minor flaw on the display system of what I otherwise thought of being a really cool tool. So, I tried to look for a e-mail contact somewhere... ANYWHERE on the company's website, and couldn't find anything resembling it, without actually shelving out a few bucks to register their scanner software from which the stats were based upon which would then grant me access to e-mailing a support technician.
And that's when my spider-sense began tingling again. And this time, I really took the time to look into it.

Figure 2. I need to pay money to tell them about a broken piece on their website? I think not.
In the light of my findings, and considering that this originally came to me as a reliable piece of security news provided from a generally trusted source (the Threatpost mailing list backed-up by Kaspersky Labs) the idea came to me to investigate the depth of the media coverage ESG received in recent years, and how they apparently managed to make a virgin image of themselves despite a shady and rocky past. As for the present, the company claims as hard as it can that it is now operating legitimately, and even threatened to take legal action against anyone pretending to the contrary, so I'll content myself with just reporting the facts the way I see them and let you, the reader, be the judge. The result of my investigation is presented in this article, and sheds some interesting lights about what I can only describe as social engineering techniques aimed at the mass medias (as opposed to a single person or small group of people) in an attempt to not only regain a certain level of apparent virginity, but also as a means to boost sales of a product of which the quality of is still matter to debate.
As a disclaimer, since there will be question of credibility a lot throughout this article, I feel that it is only fair that I provide some background info about myself. So, for the record, I got my first computer at age 12, a Commodore 64, and learned programming on that box. I later went to University, then worked as a technical support person for a couple of large companies for a few years. Then in 2000, following a burn-out, I became a self-learner security enthusiast, writing a few technical research articles and pioneering in the log management department with Open Source softwares (LogAgent, LogIDS, LogMonitor, ComLog, SIDTk) what unfortunately (for me) never got quite the buzz and support that Snort did at the time. This material has been presented in the academical conference Seguridad en Computo in Mexico City over the years of 2000-2004, in which time-frame I worked for two security companies (one of them based in Paris, France) and tried to sell a commercial version of my Open Source softwares, which never really panned out. I also did a conference in Québec City, and got invited at the Canadian Embassy in Washington as part of a government-backed IT security economical mission in the US, all in 2004. I took a break completely from computer security in 2005, and at 37 now, seeing how things have so little changed and not feeling one bit out of the loop due to my 5-years non-exposure, I am attempting my way back into it in my small-town, French-speaking birthplace. One of my softwares, ComLog has been falsely flagged as malware in the past, and may still be today, which means that I am fully aware of what it is to be put into ESG's situation. The irony of it being that it my case, ComLog is labeled as a keylogger spyware, when in fact it was designed from an admin's perspective in order to provide him with a history of commands that a hacker could be passing through cmd.exe (as this was a popular trend when IIS4 directory traversal attacks were the norm), and thus allowing him to know exactly what happened over the course of an attack, and take proper immediate action (when combined with LogAgent to centralize in real-time the logged info). A subtlety that some "anti-malware" vendors of the time, trying to build up a reputation by buffing up the number of actual "threats" detected as much as possible as a way to build street-cred, failed to see, despite my explanations to them. But I digress.
So, enough about me, and hang on to your seats folks, as you risk falling down your chair on more than one occasion as you discover some of the amazing stuff missed by the reporters of major media outlets such as CNN.com, NBC, USA Today, CNET, Information Week (http://www.enigmasoftware.com/about-us/esg-in-the-news/) and even security-aware mailing lists like Threatpost (who politely declined to follow-up on this issue) among many others, and which just proves how just about anyone can use today's "journalism laziness" to their advantage to social-engineering them into doing their own marketing campaigns for them for free, and for a product of dubious reputation thanks to its long history (ESG's SpyHunter has been around 1999), no matter what is ESG's stand on the state of its product nowadays. Some of these things are so big that it becomes obvious that any and all journalist, reporter and media outlet that jumped into the ESG bandwagon didn't do the simplest of background check on Enigma Software Group and its spokespersons and took their words for face value. Once you put together the findings gathered over about 60 websites (reached through very simple Google searches), it quickly becomes clear that ESG's credibility isn't on par with what they claim to be.

Figure 3. Some of the media outlets that have reported about Enigma Software Group
The Early Days of ESG
Going back into the story I began earlier, at the point where I was being told by the website that I had to pay for SpyHunter in order for me to hope of being able to send an e-mail to someone, a technical support contact, no less! Definitely not wanting to shelve any amount of my money just to notify this company about a small discrepancy on their website, as part of a helping gesture too, I definitely became very suspicious. Looking closer at the "data" collected by SpyHunter and reported on the malware-tracker map, I realize that this data is MUCH more partial that I thought. Of course, there is the obvious fact that this data shows only what has been gathered by one single tool on the market, which means that all infections detected by other products are not reported on this site. But more important than that, at this point, is the fact that only the "Top Ten" threats are apparently reported, and strangely enough, 8 out of 10 consist of Rogue Anti-Malwares, a common type of ransomware. Which is kind of ironic, seeing that SpyHunter was actually identified as one such Rogue Anti-Malware in the past, and still sports several characteristics of one even nowadays, despite not being listed as a Rogue software anymore. In all cases, it does seem to be a rather poor quality product compared to the norm on the market, as we will see.
I have found very little about the very early days of SpyHunter, from it's launch in 1999 to about 2004. There is a WikiPedia entry about it, but the article is labeled with a warning that the article is an orphan. The "strange wording" of the entry, as reported by the admin staff if WikiPedia makes me believe that is was written by ESG's founder himself, Alvin Estevez, or one of his employees/affiliates. Here is what it says :
I have found very little about the very early days of SpyHunter, from it's launch in 1999 to about 2004. There is a WikiPedia entry about it, but the article is labeled with a warning that the article is an orphan. The "strange wording" of the entry, as reported by the admin staff if WikiPedia makes me believe that is was written by ESG's founder himself, Alvin Estevez, or one of his employees/affiliates. Here is what it says :
SpyHunter is a proprietary computer program developed by Enigma Software Group USA, LLC that detects and removes software determined to be spyware or adware. |
The references ([1]) point to a PC Magazine review of the SpyHunter software dating back to early 2004 (http://www.pcmag.com/article2/0,2817,1524261,00.asp), and which rated the tool as a rather poor one considering the other options on the market. This is the only actual professional and independent review that I found on the web. Possibly I haven't looked deep enough, but chances are that if any review had been made about the tool that was only a tad more positive about the product, that ESG wold have touted about it on their website or somewhere else. Here are some excerpts of that review article :
|
The WikiPedia page also references an article on Mahalo.com (http://www.mahalo.com/how-to-uninstall-spyhunter-and-is-it-malware) which explains how to uninstall ESG's SpyHunter, along with providing a little bit more info on the company's stance towards how it is perceived by the IT security community.
Is Spyhunter Malware? During 2009/2010 Spyhunter is not considered malware according to the anti spyware coalition (http://www.antispywarecoalition.org/) definitions for classification as malware or spyware. |
These statements from Spybot came out of an out-of-court settlement after a lawsuit had been filled against them by ESG.
Interestingly enough, the WikiPedia entry also has a link to ESG's filings at the SEC (http://www.sec.gov/cgi-bin/browse-edgar?action=getcompany&CIK=0000799511). I am unfortunately not able to tell what's all these are about as this legal mumbo-jumbo is beyond my French-speaking self, but I guess I'll just do my own bit of lazy journalism here and make a mention of it, assuming that it bears relevancy with the rest of my analysis.
After being pointed at for more than dubious business practices in around 2004, at which time it had been labeled as a scareware producing false-positives in order to boost sales, the company by way of its president Alvin Estevez vowed to clean their act and to start doing business more ethically. However, the company's past shady reputation would prove to be a quite high hurdle to surmount, but it became quickly apparent, in an open-thread discussion with the community on a public internet forum in 2007 that the people at Enigma Software Group just didn't get what it meant do to ethical business, and all that it implied. Interestingly enough, however, I could pinpoint very exactly to two speficic posts in that thread that will prove to be the basis of ESG's new (and so far successful) "marketing" strategy that proved to be the key to their "turning over a new leaf" process.
Interestingly enough, the WikiPedia entry also has a link to ESG's filings at the SEC (http://www.sec.gov/cgi-bin/browse-edgar?action=getcompany&CIK=0000799511). I am unfortunately not able to tell what's all these are about as this legal mumbo-jumbo is beyond my French-speaking self, but I guess I'll just do my own bit of lazy journalism here and make a mention of it, assuming that it bears relevancy with the rest of my analysis.
After being pointed at for more than dubious business practices in around 2004, at which time it had been labeled as a scareware producing false-positives in order to boost sales, the company by way of its president Alvin Estevez vowed to clean their act and to start doing business more ethically. However, the company's past shady reputation would prove to be a quite high hurdle to surmount, but it became quickly apparent, in an open-thread discussion with the community on a public internet forum in 2007 that the people at Enigma Software Group just didn't get what it meant do to ethical business, and all that it implied. Interestingly enough, however, I could pinpoint very exactly to two speficic posts in that thread that will prove to be the basis of ESG's new (and so far successful) "marketing" strategy that proved to be the key to their "turning over a new leaf" process.
2007 : The New Beginning
After the scandal about the false-positives in 2004 and a somewhat similar scandal in 2005, Enigma Software Group publicly vowed to turn over a new leaf, but in reality their practices remained very closely similar to these same deceiving tactics used by actual Rogue Anti-Malware programs. An article written on April 26th 2007 by Steven Burn, from "Ur I.T. Mate group" (http://mysteryfcm.co.uk/?mode=Articles&date=26-04-2007) provides a good overview of the company's practices around that time :
How do you gather the masses to ensure your stock price goes up?, simple - ensure lots of people know about it, and scam err, have them try it. |
This article was written on the very same day that ESG, by way of CEO Alvin Estevez and Chairman Colorado Stark, made a public effort at binding ties with the anti-malware community at large and try to work out with them the problems being reproached to his software and his company. This comes as no surprise, as Steven's article had been triggered by ESG's attempt at Public Relations. This all happened in a rather revealing (even though a bit tedious and repetitive at times) thread that happened in the Spyware Warrior forum (http://spywarewarrior.com/viewtopic.php?t=24810).
I have read somewhere in all the pages I read during this investigation someone describe Alvin Estevez as a paranoid and manipulative person. Even though I do not have the credentials needed to make that sort of psychological diagnosis, there are numerous snippets in this thread that would tend to suggest so. Over the course of this thread, he also shows several times that he fails to grasp even the simplest of business ethics or even information security awareness. His opening posts already shows some signs of these tendencies :
I have read somewhere in all the pages I read during this investigation someone describe Alvin Estevez as a paranoid and manipulative person. Even though I do not have the credentials needed to make that sort of psychological diagnosis, there are numerous snippets in this thread that would tend to suggest so. Over the course of this thread, he also shows several times that he fails to grasp even the simplest of business ethics or even information security awareness. His opening posts already shows some signs of these tendencies :
|
First, we notice that they require people who wish to participate to the discussion to disclose very sensitive personal information, such as real name, address and current occupation (phone number not mentionnd but implied by many forum members) and that coming from a company who can't even provide a generic support e-mail address for people to easily reach them, and AFTER being told not to request this information by e-mail (lucky her!) by a forum admin. We can also see how Mr. Estevez wants to control the flow of the discussion in advance by selecting which topics are valid for discussion and which ones are not, and even pushing as far as trying to push its own paranoid agenda as can be seen in list item B) 3, 4 and 5. Finally, some weird disclaimer mumbo-jumbo that doesn't mean much other than not to take what ESG and it's employees may say on this forum as cash-value. Which is a kind of weird way to "come clean", in my opinion.
The actual thread mostly ran around list item A) 4 (ESG's business model), with the same questions being asked very clearly by many forum members under different tones depending on the person, which mostly got the same replies from Estevez and Stark, which was to try to re-direct the blame directed towards them onto the "smearing competitors conspirators". This ran on and on under different tones and variations before ESG representatives eventually started to lower their defensive shields and started to listen to what the community had to say.
A good example of how most of the thread went, I'll just go with the gist of MysteryFCM's first post (Steven Burn, who wrote that same-day article previously mentioned) to the thread, and Alvin's answer to it.
The actual thread mostly ran around list item A) 4 (ESG's business model), with the same questions being asked very clearly by many forum members under different tones depending on the person, which mostly got the same replies from Estevez and Stark, which was to try to re-direct the blame directed towards them onto the "smearing competitors conspirators". This ran on and on under different tones and variations before ESG representatives eventually started to lower their defensive shields and started to listen to what the community had to say.
A good example of how most of the thread went, I'll just go with the gist of MysteryFCM's first post (Steven Burn, who wrote that same-day article previously mentioned) to the thread, and Alvin's answer to it.
MysteryCFM : (...) Irrespective of the above, as has been made very clear from the numerous articles now online, and those published over the years, the main problem (as is the focus of the latest articles) are your marketing practices. |
Alvin Estevez : MysteryFCM, |
Alvin Estevez : MysteryFCM, |
Right here with this last post, we can see what is actually the main issues blamed on ESG. To Alvin Estevez, there is no problem spamming on forums with links back to "affiliates" (on domains actually owned by ESG itself) which push the SpyHunter product but not making any clear mention that it's actually SpyHunter being downloaded until you're in mid-install. The affiliates websites make no mention of SpyHunter or its maker ESG, change the binary name to something generic which furthers the camouflage of SpyHunter (which they claim as a legitimate marketing practice, but in reality it's a very poor branding practice for their product), and also claims on these affiliate websites that the software downloaded was a free "removal" tool, when in fact it was more accurate to call it a "free scanner", since you actually had to pay for any kind of malware removal to happen. These are very deceiving business practices highly similar to what classifies most Rogue Anti-Malware tools out there that SpyHunter supposedly combats as such, and Alvin Estevez fails to realize it. On top of that, he sees no differences between these dubious practices and the open collaboration on forums of reputable anti-malware specialists (his "competitors") who actually contribute factual and technically-solid information that does not try to masquerade as something else.
|
Later on, when the tension had gone down a bit, Estevez started to get the difference between forum spamming and posting actual informative articles and tried to prove his good nature by voluntarily sharing with the forum some of how own precious technical know-how by mentioning how viruses and other baddies can be removed by making a registry diff by using the System Restore functionality in Windows in order to prevent memory-resilient malwares to launch at start-up, and thus ease the manual removal process. While technically accurate, this information does not represent some sort of secret Holy Grail of anti-malware techniques to the malware experts present in the thread, nor is it new or widely used in anti-malware products.
One of TeMerc's posts contained however a prophetic promise to Alvin Estevez and ESG :
One of TeMerc's posts contained however a prophetic promise to Alvin Estevez and ESG :
Temerc : Your affiliates can blog and push their products all they like, that is not an issue. But when it is done in the manner which has been documented, by tag-teaming forums in the way I already described it, that is a problem. We in the security arena do not do that in any way shape manner or form. |
Colorado (Stark) : Hello to all. |
We can see in this last snippet and many other afterward that despite an apparent willingness to change their business practices, ESG is more interested making their current business practices "comply" with acceptable standards without actually changing them as much as possible. And as we will see later, they did quite a good job at it. The following post from eburger68 will prove to be influential in the future of ESG.
eburger68 : Alvin, |
But possibly the most important snippet of this forum thread in regards to the future of Enigma Software Group are the following two pieces from Just Bob :
Just Bob : To improve your standing you may consider the following: |
Just Bob : You may have missed the point to some degree. There's nothing wrong with being a "for profit" company. |
After a lot of fighting and arguing over the issues they are being charged with, ESG's CEO Alvin Estevez finally came to make the following statement :
Alvin Estevez : The issue of the affiliates.... we will correct this issue... we got the point. |
This did not conclude the thread, which went on for two more pages, but when one looks back at the whole thing in retrospect of the events that occurred since then, I think we can pinpoint Just Bob's and eburger68's comments as being critical to how ESG conducted business since 2007, and which in turn gave them the "mediatic virginity" needed to pass under the radar of such respected security mailing lists as ThreatPost, amongst numerous other media outlets.
Media coverage of ESG in recent years
As we just saw, the consensus was mostly that the SpyHunter application was not the issue with ESG as much as their business practices themselves. An examination of ESG's website and its network of affiliates, one could see that they didn't change that much from what they were circa 2007, which isn't too surprising considering the fact that it had been found out during that famous thread discussion that ESG's problems with the behavior of its affiliates was that ESG wasn't even enforcing its own policies on the affiliates. Better yet, Estevez didn't even know that his company already had suitable policies in place until a thread participant pointed it out to him!
A closer examination of these websites compared with snapshots of 2007, however, reveals a series of interesting minor changes, which, interestingly enough, make their website network comply to a minimum to the solutions outlined by forum participants and which we just covered in the previous section.
For example, the following things are quite notable :
A closer examination of these websites compared with snapshots of 2007, however, reveals a series of interesting minor changes, which, interestingly enough, make their website network comply to a minimum to the solutions outlined by forum participants and which we just covered in the previous section.
For example, the following things are quite notable :
- Mentions of a "Free scan" instead of a "Free Removal Tool" on all of their websites
- Downloaded executables now wear a name identifying it clearly to SpyHunter (even though the filename changes depending on the location from which it is downloaded)
- There is a mention of SpyHunter under the download links on affiliate websites
- Articles provided by their affiliates on forums now appear to have more content
However, there are also many other things that have NOT changed, and which still raises concerns about ESG's true intents about the way they do business. For example :
- Even though, technically, SpyHunter is mentioned on the affiliate websites, it is actually written so small that it is barely noticeable, which is kind of a weird thing to do when you want to get your brand product recognized by the masses. Let's not forget here that they were practically forced to clearly identify the software being downloaded, and even though they now comply, it is quite obvious that they did it to a minimum
- There is no mention whatsoever of any affiliation with ESG on the affiliates websites, other than the previously mentioned download link, while it is actually obvious that the sole purpose of these sites is to specifically push sales of SpyHunter. While not illegal, it is somewhat dishonest and deceiving as these sites pretend that they're independent from one another and free of commercial bias, when in reality it's not the case.
- The articles now provided are somewhat generic and redundant, most (if not all) of them dealing with the manual steps on how to remove a specific piece of malware. While being possibly accurate, one has to wonder of their value in the light of the rate at which new malware is produced these days. The info presented in the articles are possibly recycled from other sources, and are almost all similar since the steps to remove one piece of malware does not differ that much from the steps to remove another malware. All the malwares mentioned in the articles are actually about Rogue Anti-Malwares, which is only a small subset of the threats currently running in the wild.
- The already mentioned fact that there is not a single e-mail address to contact them on their webpage, other than forms for press or partnership inquiries, and which request for quite some sensitive information just in order to be able to send ESG a message.
- Business street addresses and phone numbers for offices in US (Florida), Lithuania (!) and South-Africa (!!) on their website, but also mentions of an address in Connecticut on SpywareWarrior.com
Figure 4. ESG's official addresses as published on their website
Alvin Estevez : |
Not that there is anything wrong with having more than one business address, but in the light of everything that's been pointed out already, along with a quick check on ESG's SpyHunter on ComplaintsBoard.com (http://www.complaintsboard.com/?search=SpyHunter&sort=date&everything=everything&page=1), and already any self-respected journalist should start thinking twice before giving media coverage to this company and its people. But through perseverance, "cleaning their act" in the ways described earlier, and as we will see later with the major help of the release of a free tool, ESG has managed to create a mediatic snowball effect over the last three years or so that is just starting now to take significant proportions. And apparently, in this day of information age, the prevalent journalistic laziness which is more and more observable these days compared to a few years ago makes it so that once a source *seems* to have passed the credential checks of another journalist, then that source immediately becomes credible to other journalists, without any of them feeling it required to double-check the background of said source.
I traced their first "major" mediatic appearance (by that, I mean "one that was not trying to depict them as potential fraudsters" as was the case in the past) to a short 3 minute presence on a program called "The Balancing Act" presented on Cable channel "Lifetime TV" aired on November 10th, 2007. In it, we see Alvin Estevez's wife Nina along with Alec Malaspina, whom I get is in charge of technical operations at ESG. It's not the "big-time" yet, but hey! It's TV, and besides, it can be recycled afterward on the web, which it was. One is not to expect a great display of technical know-how in such a short piece, and thus can not really be used to evaluate the technical expertise of these two spokespersons. I do find interesting, however, Nina Estevez's lapsus (slip of the tongue) when she says that "Spyware is software that hmm... gets infected... in your machine when you browse the web(...)". The whole thing sounds like a rehearsed act though, and this isn't that surprising as this is what one can expect from such a generic show on Cable TV. I do find it somewhat ironic however, when show host Maria Bailey warns the viewers of fraudulent marketers as she introduces Estevez and Malaspina.
I traced their first "major" mediatic appearance (by that, I mean "one that was not trying to depict them as potential fraudsters" as was the case in the past) to a short 3 minute presence on a program called "The Balancing Act" presented on Cable channel "Lifetime TV" aired on November 10th, 2007. In it, we see Alvin Estevez's wife Nina along with Alec Malaspina, whom I get is in charge of technical operations at ESG. It's not the "big-time" yet, but hey! It's TV, and besides, it can be recycled afterward on the web, which it was. One is not to expect a great display of technical know-how in such a short piece, and thus can not really be used to evaluate the technical expertise of these two spokespersons. I do find interesting, however, Nina Estevez's lapsus (slip of the tongue) when she says that "Spyware is software that hmm... gets infected... in your machine when you browse the web(...)". The whole thing sounds like a rehearsed act though, and this isn't that surprising as this is what one can expect from such a generic show on Cable TV. I do find it somewhat ironic however, when show host Maria Bailey warns the viewers of fraudulent marketers as she introduces Estevez and Malaspina.
The first news article about them listed on ESG's website dates back to August 13th, 2008, and was published in the Tech section of the USA Today (Technology Live: New York City with the Most Spyware. http://content.usatoday.com/communities/technologylive/post/2008/08/54151498/1?loc=interstitialskip). The article was about a compiled list of "most infected sites" by geographical location from which was pulled the news piece that New York was hit with the most infections. It is interesting to notice that the link provided in the article as the source to get SpyHunter actually points to one of the affiliate websites (spyware-remove.com), and not directly to enigmasoftware.com. It is also interesting that this article will base the foundation of ESG's future mediatic spin, but we aren't there yet as they're not yet applying this data onto a Google map.
The next article listed (Google Tailors YouTube for Suits http://www.ecommercetimes.com/story/64368.html?wlc=1220398260) dates back to September 2nd 2008, and is somewhat of an oddity when compared to the others listed on Enigma's website, in the way that the article doesn't speak of ESG's activity as a anti-malware vendor at all, focusing instead on the use of online video services by company execs to conduct business. It is in that light that Alvin Estevez managed to get a few quotes mentioned in the article, as shown in the following snippet from EcommerceTimes.com :
The next article listed (Google Tailors YouTube for Suits http://www.ecommercetimes.com/story/64368.html?wlc=1220398260) dates back to September 2nd 2008, and is somewhat of an oddity when compared to the others listed on Enigma's website, in the way that the article doesn't speak of ESG's activity as a anti-malware vendor at all, focusing instead on the use of online video services by company execs to conduct business. It is in that light that Alvin Estevez managed to get a few quotes mentioned in the article, as shown in the following snippet from EcommerceTimes.com :
(...) That assessment is echoed by Alvin Estevez, founder of Enigma Software Group, makers of Spyhunter security software. |
The next article was published on Investors.com on September 9th 2008 (N.Y. Region Big On Anti-Spyware, But So Is The Last Frontier, Alaska. http://www.investors.com/NewsAndAnalysis/Article/459026/200809091617/NY-Region-Big-On-Anti-Spyware-But-So-Is-The-Last-Frontier-Alaska.aspx), and was more or less based on the same piece than the first article about the New York infections, but this time also with an emphasis on Alaska.
It is then that Enigma Software Group experienced a significant shift in their mediatic marketing attempts, thanks to the "mediatic storm" that surrounded the infamous Conficker worm. Following Just Bob's advice in the forum thread mentioned earlier, ESG created a completely free removal tool specifically designed for the Conficker worm. The tool was aptly named Conficker Removal Tool. The release of this tool, the fact that it was a free removal tool as advertised and the mediatic attention that the Conficker worm gathered in the major medias made it so that Enigma software Group suddenly began receiving more media attention. They got 9 articles from various sources (DarkReading.com, Information Week, CNET News, USA Today (Tech and Money sections), CNN.com, UPI.com, CNBC) that were published between March 12 2009 and April 1 2009 solely based on the exposure ESG got through its free Conficker Removal Tool. There are other two articles that mentions them that were published in that same time-frame, but they didn't cover the Conficker worm specifically. They actually are two articles, written by the same journalist (Byron Acohido), one written for the Tech section of the USA Today and the other for The Last Watch Dog(lastwatchdog.com). One article talks about SQL injection and the other speaks of a specific case of Google Search Engine Optimization poisoning. The two articles both have in common to contain the very same exact sentence, which is also the sole reason why these articles are listed on ESG's websites.
It is then that Enigma Software Group experienced a significant shift in their mediatic marketing attempts, thanks to the "mediatic storm" that surrounded the infamous Conficker worm. Following Just Bob's advice in the forum thread mentioned earlier, ESG created a completely free removal tool specifically designed for the Conficker worm. The tool was aptly named Conficker Removal Tool. The release of this tool, the fact that it was a free removal tool as advertised and the mediatic attention that the Conficker worm gathered in the major medias made it so that Enigma software Group suddenly began receiving more media attention. They got 9 articles from various sources (DarkReading.com, Information Week, CNET News, USA Today (Tech and Money sections), CNN.com, UPI.com, CNBC) that were published between March 12 2009 and April 1 2009 solely based on the exposure ESG got through its free Conficker Removal Tool. There are other two articles that mentions them that were published in that same time-frame, but they didn't cover the Conficker worm specifically. They actually are two articles, written by the same journalist (Byron Acohido), one written for the Tech section of the USA Today and the other for The Last Watch Dog(lastwatchdog.com). One article talks about SQL injection and the other speaks of a specific case of Google Search Engine Optimization poisoning. The two articles both have in common to contain the very same exact sentence, which is also the sole reason why these articles are listed on ESG's websites.
There are numerous consumer tools designed to assess the goodness of the Web page you are about to click to, and tell you whether it’s safe. AVG, ScanSafe, McAfee and Enigma have consumer web scanning tools and services worth checking out. |
No problems so far as April Fools’ computer worm awakens. (Posted on CNN.com, April 01, 2009. http://www.cnn.com/2009/TECH/04/01/tech.viruses/index.html)
Happy Anniversary ‘Melissa;’ Next Up, Conficker!. (Posted on CNBC.com, March 26, 2009. http://www.cnbc.com/id/29897497)
Conficker Cabal goes after computer worm. (Posted on UPI.com, March 25, 2009. http://www.upi.com/Top_News/2009/03/25/Conficker-Cabal-goes-after-computer-worm/UPI-14801237929348/)
Cybersheriffs arm selves for Conficker showdown. (Newspaper article from USATODAY, March 25, 2009. http://www.enigmasoftware.com/news/usatoday/cybersheriffs-arm-selves-for-conficker-showdown.pdf)
No joke in April Fool’s Day computer worm. (Posted on CNN.com, March 24, 2009. http://www.cnn.com/2009/TECH/03/24/conficker.computer.worm/index.html)
PC security forces face April 1 showdown with Conficker worm. (Posted on USATODAY.com, March 24, 2009. http://www.usatoday.com/tech/news/computersecurity/wormsviruses/2009-03-24-conficker-computer-worm_N.htm)
Hackers poison PCs that Google “March Madness”. (Posted on USATODAY.com, March 18, 2009. http://blogs.usatoday.com/technologylive/2009/03/hackers-poison.html)
FAQ: The rapid spread of SQL injection attacks. (Posted on LastWatchdog.com, March 17, 2009. http://lastwatchdog.com/faq-sql-injection-attacks/)
Latest Conficker worm gets nastier. (Posted on CNet.com, March 13, 2009. http://news.cnet.com/8301-1009_3-10196122-83.html)
No Fooling: Conficker Set To Strike April 1. (Posted on InformationWeek.com, March 13, 2009. http://www.informationweek.com/blog/main/archives/2009/03/no_joke_confick.html)
Conficker/Downadup Evolves To Defend Itself. (Posted on DarkReading.com, March 12, 2009 http://www.darkreading.com/security/vulnerabilities/showArticle.jhtml?articleID=215900041)
Then, the next article on ESG's website is somewhat of an oddity, definitely something that sticks out of the lot here, and which I will actually treat with more detail in the next section of this article, as to not spoil the surprise. (Even dirtier IT jobs: The muck stops here http://www.infoworld.com/d/adventures-in-it/even-dirtier-it-jobs-muck-stops-here-002?page=0,4)
Finally, the latest breakthrough from Enigma Software Group that made it so for ESG to not only get more mediatic coverage, but also gain enough "mediatic virginity" in the light of its shady past to make it past the credibility checks of security mailing lists such as ThreatPost, as was reported at the beginning of this article : the Malware Tracker Map.
Finally, the latest breakthrough from Enigma Software Group that made it so for ESG to not only get more mediatic coverage, but also gain enough "mediatic virginity" in the light of its shady past to make it past the credibility checks of security mailing lists such as ThreatPost, as was reported at the beginning of this article : the Malware Tracker Map.
Atlanta Has Dubious Honor of Highest Malware Infection Rate. (Posted on News.Yahoo.com, July 06, 2010 http://news.yahoo.com/s/pcworld/20100706/tc_pcworld/atlantahasdubioushonorofhighestmalwareinfectionrate)
Atlanta Has Dubious Honor of Highest Malware Infection Rate. (Posted on PCWorld.com, July 06, 2010 http://www.pcworld.com/businesscenter/article/200555/atlanta_has_dubious_honor_of_highest_malware_infection_rate.html)
At Least 1380 Suspected Infected PC in Mauritius. (Posted on IslandCrisis.net, June 07, 2010 http://www.islandcrisis.net/2010/06/1380-infected-pc-mauritius/)
Malware Tracker Map Gives Live Worldwide Coverage of Infected Computers. (Posted on FastCompany.com, May 27, 2010 http://www.fastcompany.com/1653015/malware-tracker-map-gives-live-worldwide-coverage-of-infected-computers)
Malware Tracker Map – bird’s eye view of nasty software from bad people. (Posted on RedFerret.net, May 27, 2010 http://www.redferret.net/?p=21425)
Not present on the list of articles featured on ESG's website is also the article from which this whole investigation started, originally published on HelpNetSecurity and referred two days later on the ThreatPost mailing list :
Southern Cities Have High Malware Rates. (Posted on HelpNetSecurity, June 25, 2010 http://www.net-security.org/malware_news.php?id=1385)
This means that there are possibly other articles reporting more or less on the same topic out there on the web that have simply fallen through the cracks.
What are these articles about, actually? The first one of this series, published on RedFerret blog, is simply a post made of a two-sentences presentation of the Malware Tracker Map written by "Nigel" under a screen-capture picture of said Malware Tracker Map, along with a snippet obviously copied-and-pasted directly from Enigma's Website :
What are these articles about, actually? The first one of this series, published on RedFerret blog, is simply a post made of a two-sentences presentation of the Malware Tracker Map written by "Nigel" under a screen-capture picture of said Malware Tracker Map, along with a snippet obviously copied-and-pasted directly from Enigma's Website :
|
The next article on FastCompany is more or less of the same thing, with actually three short paragraphs of text from the author (Addy Dugdale), with whom I'd tend to mostly agree with what he says in his third and last paragraph :
|
Things become more interesting after that, as we can see a trend growing in the following articles, which is the snow-balling effect that I was referring to earlier. They all are more or less a recycling of some of their earlier mediatic attempts, when they had statistics showing infection rates for New-York and Alaska. Once the same type of news piece is wrapped with the visuals of the Malware Tracker Map, it suddenly becomes a more eye-catchy piece for Enigma to get spoken about them in media outlets, especially since they actually provide a very demanded commodity, malware infection rates in some geographical areas where it was previously impossible to collect such data. Like Mauritius, for example, as seen in the article from IslandCrisis.Net, or Eastern Québec in my case. The remaining articles revolve around the same theme, this time focusing on the "studied observation" that cities in the Southern part of the U.S. have higher malware infection rates than their Northern counter-parts. That last topic seems to gather enough interest from media outlets to see several articles based on that single news piece, reporting this info as reliable facts.
But let us take a small breather here and look back at what we've discovered so far, shall we?
What we're seeing here is a supposedly-legitimate company who has had more than its fair share of controversy in its history, having a long past of shady marketing tactics that are somewhat ironically very similar to those very same malware (most of them actually being Rogue Anti-Malwares) that it claims to combat. We are talking of a company who up until very recently had very little peer-credibility, and which was made highly public on the net. We're talking of a business that despite complying to some very basic guidelines provided kindly by forum users, didn't fundamentally change it's business model that seems to be based at least partly on deception, and which the customer base seems to be part of the most gullible portion of the population at large (as Alvin Estevez quotes : his customers don't like to read!). And finally, we are talking of a company that gained most of its "mediatic credibility" thanks to the creation of a free removal tool meant for one single piece of malware. Not that there is anything wrong with that, but in terms of impact in the industry, we're far from widely-reputed and impactful softwares like Snort, Metasploit or nmap to name a few. What we are seeing is media outlets failing to make the proper credibility checks before giving exposure to so-called experts through their channels, based on the fact that other stories have been wrote on them in the past, notwithstanding the fact that some of these past "mediatic references" as actually as thin as paper. So, basically, what we are actually seeing, in my opinion, is a group of possible online scam artists managing to gain visibility and credibility to the masses at large via the means of cleverly social-engineering major media outlets of the web, papers and even television.
Note here that I used verbs like "seem" and adjectives like "possible" in that last paragraphs. After all, there IS a possibility that ESG is indeed trying its darnedest to do business legitimately, but are just doing a very poor job of it. But my point here is that at the light of everything that's been dug out so far, any self-conscious journalist who actually goes through the trouble of doing a few simple Google searches to verify the credibility of a source he considers for one of his articles would, or at least should, have had some concerns at this point and check in a little deeper before granting media-exposure to such an organization. I, personally and given ESG's past doubtful ways of doing marketing, have issues concerning the validity of the data presented on the Malware Tracker Map, and by extension, the validity of any news story based on interpretations of that data. I will cover these issues in more details a bit later.
But for now, let me be the Devil's Advocate here and pretend that there is nothing fundamentally flawed in ESG's marketing and web presence, let's pretend that the company is now acting in such an ethical way that its past problems can now be easily forgotten and forgiven without giving it any other second thought, and let's pretend that the company's contribution to the security community and industry has been significant enough to be referred to as being an expert in the security field, one upon which a media outlet can rely to produce a reliable and credible news article. In short, let's pretend that all that I have pointed out so far as "sticking out" doesn't really matter and doesn't properly reflect the company's current state, and that these media outlets were "in the right" when they granted access to their channels to ESG and its representatives.
Let's pretend that there is no reason to be concerned so far with what I exposed from ESG passing through the credibility checks of some of the biggest media outlets out there...
Then, let's have a closer look at the actual people behind ESG's operations, just to see what else these medias may have missed.
But let us take a small breather here and look back at what we've discovered so far, shall we?
What we're seeing here is a supposedly-legitimate company who has had more than its fair share of controversy in its history, having a long past of shady marketing tactics that are somewhat ironically very similar to those very same malware (most of them actually being Rogue Anti-Malwares) that it claims to combat. We are talking of a company who up until very recently had very little peer-credibility, and which was made highly public on the net. We're talking of a business that despite complying to some very basic guidelines provided kindly by forum users, didn't fundamentally change it's business model that seems to be based at least partly on deception, and which the customer base seems to be part of the most gullible portion of the population at large (as Alvin Estevez quotes : his customers don't like to read!). And finally, we are talking of a company that gained most of its "mediatic credibility" thanks to the creation of a free removal tool meant for one single piece of malware. Not that there is anything wrong with that, but in terms of impact in the industry, we're far from widely-reputed and impactful softwares like Snort, Metasploit or nmap to name a few. What we are seeing is media outlets failing to make the proper credibility checks before giving exposure to so-called experts through their channels, based on the fact that other stories have been wrote on them in the past, notwithstanding the fact that some of these past "mediatic references" as actually as thin as paper. So, basically, what we are actually seeing, in my opinion, is a group of possible online scam artists managing to gain visibility and credibility to the masses at large via the means of cleverly social-engineering major media outlets of the web, papers and even television.
Note here that I used verbs like "seem" and adjectives like "possible" in that last paragraphs. After all, there IS a possibility that ESG is indeed trying its darnedest to do business legitimately, but are just doing a very poor job of it. But my point here is that at the light of everything that's been dug out so far, any self-conscious journalist who actually goes through the trouble of doing a few simple Google searches to verify the credibility of a source he considers for one of his articles would, or at least should, have had some concerns at this point and check in a little deeper before granting media-exposure to such an organization. I, personally and given ESG's past doubtful ways of doing marketing, have issues concerning the validity of the data presented on the Malware Tracker Map, and by extension, the validity of any news story based on interpretations of that data. I will cover these issues in more details a bit later.
But for now, let me be the Devil's Advocate here and pretend that there is nothing fundamentally flawed in ESG's marketing and web presence, let's pretend that the company is now acting in such an ethical way that its past problems can now be easily forgotten and forgiven without giving it any other second thought, and let's pretend that the company's contribution to the security community and industry has been significant enough to be referred to as being an expert in the security field, one upon which a media outlet can rely to produce a reliable and credible news article. In short, let's pretend that all that I have pointed out so far as "sticking out" doesn't really matter and doesn't properly reflect the company's current state, and that these media outlets were "in the right" when they granted access to their channels to ESG and its representatives.
Let's pretend that there is no reason to be concerned so far with what I exposed from ESG passing through the credibility checks of some of the biggest media outlets out there...
Then, let's have a closer look at the actual people behind ESG's operations, just to see what else these medias may have missed.
Background check of ESG's "core staff"
Following my findings about Enigma Software Group as a corporate entity, I decided to take a closer look at some of the individuals actually behind this operation. After all, the company did claim in 2007 that it wanted to prove the legitimacy of their business, saying that it had learned from its errors made in the past. Now, a corporate entity being just that, it's hard to evaluate the credibility of such claims by being outside the walls of said corporate entity. Thus, it seemed logical from this perspective to see if I could dig some extra info on some of the people who spoke publicly on behalf of ESG. My focus came down to 4 people in particular : Alvin Estevez himself (CEO), Alessandro Malaspina (CTO), Patrick Morganelli (Senior VP Technology) and Kristopher Dukes (status unclear).
So, I fired up my trusty Firefox and launched a few more searches on those names. Here's what I found.
So, I fired up my trusty Firefox and launched a few more searches on those names. Here's what I found.
Alvin Estevez :
We've covered in part the colorful personality of Alvin Estevez earlier already when we saw in the forum thread of 2007 some highly distinctive traits of how he does not seem to grasp even some of the most e-marketing netiquette and ethical business practices, delving at times in the realm of conspiracy theories of coordinated smearing campaigns targeted at his product and company, amongst other things.
I think that at this point, it is worthwhile to take a look at his own profile on business-oriented social-networking sites like Linked-In and Spoke.com.
I think that at this point, it is worthwhile to take a look at his own profile on business-oriented social-networking sites like Linked-In and Spoke.com.
|
Now, it is interesting to see that he is since 2006 the co-founder of a company that started its operations in 1999, and that he's been involved with it since the beginning. I don't know quite well what this actually means, but just like so many other things about Alvin, I thought that it was worthy of mention. It is also interesting to note that the business address for ESG listed on these two sites is located... in New York! Seems to me that they are changing locations quite a lot.
There isn't that much more interesting information on these two pages, however. What is actually interesting about Estevez, is when he goes public, like in the following excerpts from the same thread we looked at earlier. Mind you, this all happened AFTER Alvin apparently understood the error of his previous ways, the point at which I stopped my reporting of that thread in the earlier section of this article :
There isn't that much more interesting information on these two pages, however. What is actually interesting about Estevez, is when he goes public, like in the following excerpts from the same thread we looked at earlier. Mind you, this all happened AFTER Alvin apparently understood the error of his previous ways, the point at which I stopped my reporting of that thread in the earlier section of this article :
Alvin Estevez : The issue of the affiliates.... we will correct this issue... we got the point. |
.... I will find the balance between business driven performance (sell, sell sell) and good ethics...... And keep the sales guys in check.... |
My app is a good app..... It is very adaptive... even if many spyware components are not detected in the first scan..... The user has a "one-button-support-log" feature to report the components to us. We then add the missing pieces and remove the parasite.... We are working to make the product better. |
If we want to put out informative articles, you are saying we cannot do it? |
Just like there are many things I do not understand about your world. |
TeMerc, |
Quote: |
Alvin Estevez : |
Suzi (Site Admin) : I think you are mistaken on your interpretation of that thread at Cnet. I don't see any vendors pushing their own products there. |
Alvin Estevez : I think that sounds like a broken record.... |
The thread was officially closed shortly after that for "entering into Kool-Aid territory", as Alvin's paranoid tendencies can be clearly seen in these closing words of his. Now, mind you, all snippets taken from this thread are but only a portion of the whole thing, and I chose only the most demonstrative parts of it.
OK, so Alvin Estevez has a very poor understanding of proper internet marketing practices in the field of computer security products. Maybe he is more of a techie, and not so much of a business suit, learning the hard way of the corporate antics? Well, I considered that as a possibility until I fell on that other blog post and ensuing thread on certifiedbug.com about whether or not ESG's website had been spoofed (http://certifiedbug.com/blog/2008/05/21/enigmasoftware-payday-loan/) :
OK, so Alvin Estevez has a very poor understanding of proper internet marketing practices in the field of computer security products. Maybe he is more of a techie, and not so much of a business suit, learning the hard way of the corporate antics? Well, I considered that as a possibility until I fell on that other blog post and ensuing thread on certifiedbug.com about whether or not ESG's website had been spoofed (http://certifiedbug.com/blog/2008/05/21/enigmasoftware-payday-loan/) :
|
Now, what struck the most odd at me first when reading this thread was how nonchalantly Alvin Estevez was apparently brushing off the issue of his server being exploited, more concerned about rumors spreading about ESG becoming a loan and financing company rather than the impact of ESG's reputation as a computer security company after their webserver falling to such a common exploit as a cross-site scripting attempt! Notice how he uses twice the word "simply" to address this situation. We can also clearly see Alvin's paranoid and aggressive tendencies in this bit also, immediately jumping at the gun to shoot the messenger and right off accusing the people at certifiedbug.com to be behind this whole incident, whereas they were simply reporting it, and then completely avoiding the issue when being pointed out to him.
This must be how Alvin "builds strong relationships with employees, partners, and vendors", as he puts it himself in his LinkedIn profile.
In my eyes, Alvin Estevez has very little, if at all, credibility in the field of computer security.
This must be how Alvin "builds strong relationships with employees, partners, and vendors", as he puts it himself in his LinkedIn profile.
In my eyes, Alvin Estevez has very little, if at all, credibility in the field of computer security.
Alessandro (Alec) Malaspina
Enigma's Chief Technology Officer Alessandro Malaspina is the person who appeared with Nina Estevez in that cable-TV clip we saw earlier. I was curious to see what I would find out about him when I started googling his name, and much to my deception, I didn't find that much "dirt" on him. An actual look at his resume (http://www.alecmalaspina.com/resume.htm) shows that he does indeed seem to have some credible technical background. But let's focus on the parts that are actually relevant to our study of Enigma Software Group.
PROFESSIONAL EXPERIENCE |
I joined Enigma Software Group in January 2004. |
At first sight, these seemed like very optimistic numbers to me, but then again, maybe these numbers are genuine as well. On a typical 8-hours workday, each technical support agent would be answering and resolving tickets at an average pace of one ticket each 5 minutes. This may not be impossible, but still makes me wonder on the stress levels of these agents at the end of a typical week, especially considering that computer security and malware infections isn't as trivial as Alvin Estevez would like to make it look like at times. But without further clues on this one, I have but no choice but to give the benefit of the doubt to Malaspina.
However, I am not sure I can say the same of Alvin Estevez when, in that forum thread from 2007, he says :
However, I am not sure I can say the same of Alvin Estevez when, in that forum thread from 2007, he says :
We get over 5,000 tickets a day.... for issues above and beyond spyware.... We even have custom fixes for viruses ...... |
If I was worried of the stress level of ESG'S 5 customer support agents with a volume of 500 tickets per day, what should I think when Alvin mentions that they are actually dealing with 10 times more volume?
I also wonder what actually prevents Alvin from publishing all the "thank you letters" he receives from his customers. I am sure, however, that they are not the same people who posts their impressions of ESG and its software on ComplaintsBoard.com (http://www.complaintsboard.com/?search=SpyHunter&sort=date&everything=everything&page=1).
One could assume that between the time Malaspina wrote his resume on his website and that forum thread from 2007, SpyHunter's sales skyrocketed, resulting in higher volumes of trouble tickets, and in return, the hiring of additional agents. That could almost be a valid argument, if it weren't for that snippet I found from a Registration Statement (Form SB-2/A ) filed in at the Securities and Exchange Commission on March 26th 2007 (http://google.brand.edgar-online.com/EFX_dll/EDGARpro.dll?FetchFilingHTML1?ID=5056087&SessionID=SNHoHeDu1Wnqz77) :
I also wonder what actually prevents Alvin from publishing all the "thank you letters" he receives from his customers. I am sure, however, that they are not the same people who posts their impressions of ESG and its software on ComplaintsBoard.com (http://www.complaintsboard.com/?search=SpyHunter&sort=date&everything=everything&page=1).
One could assume that between the time Malaspina wrote his resume on his website and that forum thread from 2007, SpyHunter's sales skyrocketed, resulting in higher volumes of trouble tickets, and in return, the hiring of additional agents. That could almost be a valid argument, if it weren't for that snippet I found from a Registration Statement (Form SB-2/A ) filed in at the Securities and Exchange Commission on March 26th 2007 (http://google.brand.edgar-online.com/EFX_dll/EDGARpro.dll?FetchFilingHTML1?ID=5056087&SessionID=SNHoHeDu1Wnqz77) :
(...) |
Far from skyrocketing sales, the company almost predicts that sales are expected to die (phase out?) in 2007 or 2008. The numbers simply don't add up, and given the ten-fold discrepancy between Malaspina's and Estevez's numbers, I think it is clear here that someone is lying... or at the very least bending the truth a little.
I do find it amusing, however, that ESG's conception of something as complex as computer security can be compared to a Fisher-Price toy. This is a huge contrast compared to anyone else in the industry who outlines regularly the complexity of the various problems involved in info-sec. This, in my eye, also hinders their credibility as a company.
I do find it amusing, however, that ESG's conception of something as complex as computer security can be compared to a Fisher-Price toy. This is a huge contrast compared to anyone else in the industry who outlines regularly the complexity of the various problems involved in info-sec. This, in my eye, also hinders their credibility as a company.
Patrick Morganelli
Patrick Morganelli is listed on LinkedIn as ESG's Senior Vice President, Technology since 2003. No other previous job experiences are listed on his public profile. The reason why I got interested in Morganelli's case is because he was ESG's spokesperson in the article "Even dirtier IT jobs: The muck stops here" (http://www.infoworld.com/d/adventures-in-it/even-dirtier-it-jobs-muck-stops-here-002?page=0,4), which I mentioned earlier without revealing too much details about it. This article is a follow-up on a previous piece titled "Dirty IT jobs", and focuses on the less-glamorous parts of being an I.-T. expert. The dirty job in question here being that of the fearless malware hunter.
Dirty IT job No. 5: Fearless malware hunter |
So, for Morganelli, malware is tightly related to the most disturbing porn sites out there on the web, almost implying that those people who do get infected by malware are actually lust-filled sexually-deviant people(!). This highly contrasts with the second part of this "job coverage" in this article as the quotes comes from the much more reputable malware specialist Andrew Brandt, from Webroot.
Andrew Brandt, a malware researcher and blogger for security software vendor Webroot (and InfoWorld chronicler of IT admin gaffes, stupid hacker tricks, and colossal QA oversights), says he was warned before he took the job that he'd see porn that would turn his stomach. But he says he sees less malware distributed via porn sites and more via fake BitTorrents and game cheats sites. |
Even though not as sensationalist as Morganelli's quotes, Andrew Brandt seems to me like he is more describing what I would expect from a true malware expert than some story about some easily-shocked prude. In all the presentations made during conferences made by independent security researchers and commercial vendors alike that I have had the chance to attend have I ever heard any one of them put such emphasis (if any!) on the prevalence of the darkest gore and porn sites as being the major platforms for malware distribution. I'm not saying that there isn't any, just that its importance is highly exaggerated by ESG'S Morganelli, in what I perceive as an attempt at sensationalistic journalism on par with ESG's other marketing practices.
Kristopher Dukes
Now, this is quite litteraly the proverbial cherry on top of the sundae, so to speak, which finally convinced me that I was actually onto something here, and not just wasting time battling windmills. I found out about her a little by accident, as I was searching on YouTube for video material concerning ESG. She featured as a "product specialist" for Enigma's SpyHunter software and as a "computer virus expert" in a televised news piece broadcasted on WNBC in the wake of the Conficker worm in 2009. Why is this video NOT present on ESG's website as part of the media references is beyond me.
I haven't found any references of Kristopher Dukes in any of the business operatives of Enigma Software Group. Dukes is identified as the founder of anti-malware website 411-spyware.com (http://www.thesmilingpirate.com/category/antivirus-antispyware-antimalware/), which is one of ESG's affiliates domain. Now, knowing that ESG has blamed most of its spamvertising campaigns on its affiliates in the past, coupled with the fact that ESG actually owns the affiliate domain names, one can only speculate as to the real nature of the business relationship between Dukes and ESG. Affiliate? Employee? Consultant? Unclear. Especially that now, 411-spyware.com now redirects to fasterpccleanclean.com, still mainly operated by Kristopher Dukes, but which now seems to be pushing SpyDoctor, a competitor of ESG.
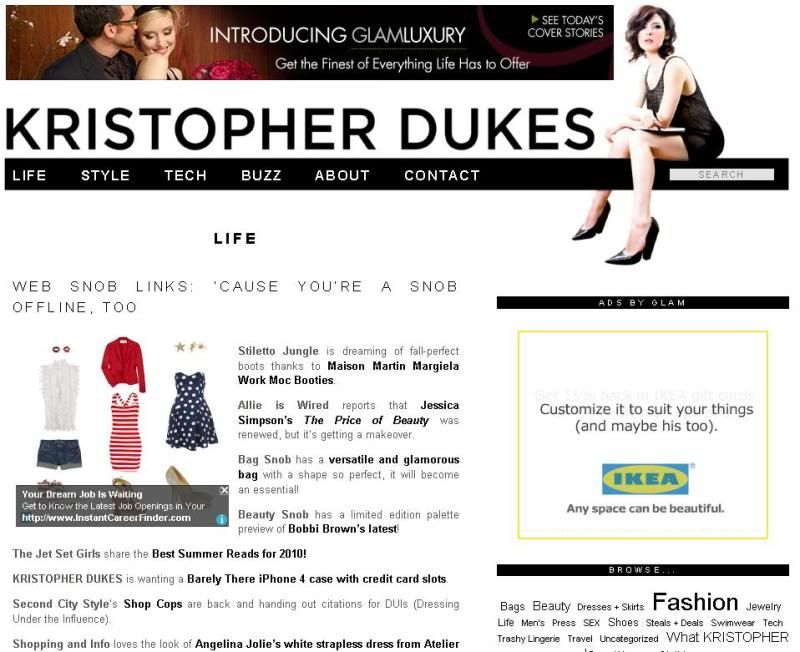
Figure 5. Kristopher Dukes blog. Is this really the same person? Yes it is.
However, 411-spyware.com isn't the first website I came upon when I googled Kristopher's name. The first site that came up was her own personal blog (http://www.kristopherdukes.com). Even though there is a small Tech section which mostly covers electronic gadgets like iPhones, this site is predominantly about one thing : fashion! Up to a point where I began wondering if I was actually at the right person's website. Her bio did nothing to convince me of the contrary :

Figure 5. Kristopher Dukes blog. Is this really the same person? Yes it is.
However, 411-spyware.com isn't the first website I came upon when I googled Kristopher's name. The first site that came up was her own personal blog (http://www.kristopherdukes.com). Even though there is a small Tech section which mostly covers electronic gadgets like iPhones, this site is predominantly about one thing : fashion! Up to a point where I began wondering if I was actually at the right person's website. Her bio did nothing to convince me of the contrary :
My passions in life are writing and beauty, and combining the two in storytelling. |
Absolutely no mention of any involvement in anti-malware whatsoever, to a point where one has to wonder how important are her involvements in the anti-malware community in the big picture of her life. Because don't be mistaken, it IS the very same Kristopher Dukes that we are talking about here. I traced her back to a few blogs, where she appears to be a contributor as an article writer, namely on ThisNext.com (http://www.thisnext.com/by/KRiSTOPHERDUKES/) and BestCovery.com (http://www.bestcovery.com/user/295).
Her bio profile on BestCovery.com actually sums up best just how relevant and credible Kristopher Dukes is in the info-sec and anti-malware community at large :
Her bio profile on BestCovery.com actually sums up best just how relevant and credible Kristopher Dukes is in the info-sec and anti-malware community at large :
Kristopher Dukes (kristopherdukes) |
Yep! You've read that last part right :
Fashion and cybersecurity may see like very different topics, but both blogs go back to a core focus of my career -- |
But you don't have to take my word for it. You don't even have to go check the linked references to verify on the original webpages that I am not actually trying to pull you, the reader, a fast one. All you have to do is take Kristopher's own words on it :
"The Martha Stewart of Technology" (knowing that Stewart did jail time isn't too re-assuring), to "fight cyber-crime and have really exceptional hair" and comparing herself to "Mother Theresa in a mini-skirt", no less! Storytelling is definitely her strong suit.
I, for one, would not know of any single info-sec specialist, male or female, who would go to such lengths about bragging that his/her goal in life is to work from home in under-wear, as appealing as the idea may sound.
This, I think, is the final nail in the coffin of ESG's credibility.
I, for one, would not know of any single info-sec specialist, male or female, who would go to such lengths about bragging that his/her goal in life is to work from home in under-wear, as appealing as the idea may sound.
This, I think, is the final nail in the coffin of ESG's credibility.
Current posture of ESG - Failing to see the irony
As it stands today, SpyHunter isn't classified as scareware on most list anymore. It does seem indeed that the tool is no longer reporting false infections in order to boost sales of the product, like it did for a time in the earlier part of the first decade of the millennium. But closer inspection to the tool and especially at how it is marketed shows that SpyHunter, and the company behind it (ESG) sports several features that could be used to classify it as a rogue anti-malware, or scareware.
For instance, other than the PC Magazine review it got in which it was described as a mediocre product, I found several user reviews stating that SpyHunter either failed to detect, or even remove (once it was paid for) some of the very same pieces of malware it claims to be removing through its advertising. In the light of this, maybe that SpyHunter doesn't classify as a malware in itself, but in my opinion it easily ranks as Snake-Oil software, and thus something I'd hardly recommend to anyone. But whether or not Spyhunter is a fraudulent software is beyond the issue here, as it is ESG's marketing practices that are borderline fraudulent, and which poses the serious question as to whether or not the large media outlets do the proper background checking on their sources before citing them in interview pieces and articles.
Why am I saying that ESG's marketing practices are still at the very least "borderline" fraudulent as of today? Well, mostly because most of their marketing is based on a set of "affiliate" websites that appear to be independent of ESG, but are in reality created for the sole purpose of pushing ESG's products, trying to mimic what is being made in other legitimate websites and forums, in order to create a cloak of false credibility around their product SpyHunter in hopes to convince websurfers to click the download link to their tool. The big problem here being that these sites try to make believe that they are independent when in fact they are not, which is a deceiving tactic that could easily be classified as false representation. On top of that, this is one of the actual tactics used by scareware authors to lure users into trusting their tool, by providing them with a simulacrum of "peer review" that couldn't be obtained otherwise.

Figure 6. Enigma Software Group Logo. Notice how similar it is with SpywareRemove's logo.
Figure 7. SpywareRemove.com's main page. Notice how small is the SpyHunter label compared to the mention of a "Spyware Scan".
Figure 8. The download button included into SpywareRemove.com's articles is more clear, however.
Figure 9. Anti-Spyware-101.com main page. Here too, more emphasis on the "Spyware Scanner" than on the brand name of SpyHunter.
Figure 10. Here too it gets more clear once you see the download button embedded into the articles.
Then, there is the whole marketing based on the publishing of articles on these sites (as well as others, which was the source of the spamvertising complaints of 2007), which consists of the same articles being recycled over and over on each of these affiliate sites. Other than being very short and little informative, these articles also bug me in the sense that this seems a very strange marketing strategy to me in the light of the current known malware propagation rates, which are hovering around the 1 500 000 mark of new pieces of malware found each month. Seems to me that such a marketing effort will only have as much success as the infection rates of the specific pieces of malware covered in these articles, which is more than hit-and-miss considering the daily volume of known new malware. Unless, of course, that you're also coordinating in some way the propagation of said pieces of malware, knowing that the people getting infected with it will find your pages when looked up in search engines, thus ensuring a constant flow of new visitors to your relatively unknown and poor reputable product. That, in a sense, is not that different from the strategy behind the MonaRonadona scareware scam (http://www.securelist.com/en/blog/208187485/MonaRonaDona_malware and http://www.prevx.com/blog/82/MonaRonaDona--We-might-be-in-the-AV-industry-but-at-least-we-arent-STUPID.html). I am not saying that this is actually the case, as I haven't pushed my investigations that far, but in the light of ESG's past practices and the elasticity of their ethical principles, we are justified to have a reasonable doubt on the issue.
Figure 11. PCthreat.com main page. Cool little Lego guys. Here, it is clear the link is about SpyHunter, and not some other scanner.
Figure 12. It is MUCH less clearer in the download link contained inside their articles. And yes, this will download SpyHunter. I tried it, just to be sure.
The same logic applies to the video advertisements they made for the web, like this one, for example, which lays it rather thick on the F.U.D. and drama, a known favorite selling vector for snake-oil vendors :
For instance, other than the PC Magazine review it got in which it was described as a mediocre product, I found several user reviews stating that SpyHunter either failed to detect, or even remove (once it was paid for) some of the very same pieces of malware it claims to be removing through its advertising. In the light of this, maybe that SpyHunter doesn't classify as a malware in itself, but in my opinion it easily ranks as Snake-Oil software, and thus something I'd hardly recommend to anyone. But whether or not Spyhunter is a fraudulent software is beyond the issue here, as it is ESG's marketing practices that are borderline fraudulent, and which poses the serious question as to whether or not the large media outlets do the proper background checking on their sources before citing them in interview pieces and articles.
Why am I saying that ESG's marketing practices are still at the very least "borderline" fraudulent as of today? Well, mostly because most of their marketing is based on a set of "affiliate" websites that appear to be independent of ESG, but are in reality created for the sole purpose of pushing ESG's products, trying to mimic what is being made in other legitimate websites and forums, in order to create a cloak of false credibility around their product SpyHunter in hopes to convince websurfers to click the download link to their tool. The big problem here being that these sites try to make believe that they are independent when in fact they are not, which is a deceiving tactic that could easily be classified as false representation. On top of that, this is one of the actual tactics used by scareware authors to lure users into trusting their tool, by providing them with a simulacrum of "peer review" that couldn't be obtained otherwise.

Figure 6. Enigma Software Group Logo. Notice how similar it is with SpywareRemove's logo.

Figure 7. SpywareRemove.com's main page. Notice how small is the SpyHunter label compared to the mention of a "Spyware Scan".

Figure 8. The download button included into SpywareRemove.com's articles is more clear, however.

Figure 9. Anti-Spyware-101.com main page. Here too, more emphasis on the "Spyware Scanner" than on the brand name of SpyHunter.

Figure 10. Here too it gets more clear once you see the download button embedded into the articles.
Then, there is the whole marketing based on the publishing of articles on these sites (as well as others, which was the source of the spamvertising complaints of 2007), which consists of the same articles being recycled over and over on each of these affiliate sites. Other than being very short and little informative, these articles also bug me in the sense that this seems a very strange marketing strategy to me in the light of the current known malware propagation rates, which are hovering around the 1 500 000 mark of new pieces of malware found each month. Seems to me that such a marketing effort will only have as much success as the infection rates of the specific pieces of malware covered in these articles, which is more than hit-and-miss considering the daily volume of known new malware. Unless, of course, that you're also coordinating in some way the propagation of said pieces of malware, knowing that the people getting infected with it will find your pages when looked up in search engines, thus ensuring a constant flow of new visitors to your relatively unknown and poor reputable product. That, in a sense, is not that different from the strategy behind the MonaRonadona scareware scam (http://www.securelist.com/en/blog/208187485/MonaRonaDona_malware and http://www.prevx.com/blog/82/MonaRonaDona--We-might-be-in-the-AV-industry-but-at-least-we-arent-STUPID.html). I am not saying that this is actually the case, as I haven't pushed my investigations that far, but in the light of ESG's past practices and the elasticity of their ethical principles, we are justified to have a reasonable doubt on the issue.

Figure 11. PCthreat.com main page. Cool little Lego guys. Here, it is clear the link is about SpyHunter, and not some other scanner.

Figure 12. It is MUCH less clearer in the download link contained inside their articles. And yes, this will download SpyHunter. I tried it, just to be sure.
The same logic applies to the video advertisements they made for the web, like this one, for example, which lays it rather thick on the F.U.D. and drama, a known favorite selling vector for snake-oil vendors :
I do find utterly funny the voice-over edit towards the end, which sounds just like the parody of a crooked advertisement taken right out of a Simpsons episode. They also produced a series of other such small videos, this time with the same philosophy than with the articles in mind : recycling and getting exposure based on very specific pieces of malware. In this case, VirusBurst :
Less dramatic and more demonstrative, a similar video about AntiVirGear quickly shows the futility and redundancy of such video productions. Scanning a system for malware is much akin in terms of entertainment as watching a software install, and most people will agree that once you've seen a progress bar make it's progression to 100%, you've seen them all.
And these are just a sample of more similar videos. The final thing that likens SpyHunter to other scarewares so much is the fact that it claims that a free trial is available, while in fact it's only the scanning that is free. You have to pay to remove any found item flagged as potentially malicious. This just isn't quite the same thing as a, say, fully-featured trial period of 30 days, which is something commonly seen. Seeing that SpyHunter makes no discrimination between a rogue anti-malware and a simple cookie, what you thought started out as a "free trial" quickly ends up with software asking you to shelve out some money to get rid of a couple of harmless cookies. Knowing that ESG targets "people who don't like to read", and that there's no e-mail on their website to even direct a simple question, it's easy to see that the most gullible portion of the population exposed to SpyHunter may actually panic and fall for the trick.
But the irony doesn't stop there. At first, the new "SpyHunter's Helpdesk Service" they now offer to the paying customers came to me as yet another sign of SpyHunter being Snake Oil software. If the software is as good as it's author claims it to be, then there wouldn't be such an emphasis put on that support service, and its ability to create custom fixes "just for your computer", which sounds like a bogus claim at best. I later found out reports from users who mentioned trying to call this support helpdesk, only to get no answer or to get rudely hung up upon. Which brings back questions about the legitimacy of the whole thing.
It turns out that ESG seems to be pretty proud of this support service, and don't hesitate to push it a lot publicly, as could be seen in some of Alvin's previously quoted comments, or in this newer advertisement for SpyHunter 4 :
But the irony doesn't stop there. At first, the new "SpyHunter's Helpdesk Service" they now offer to the paying customers came to me as yet another sign of SpyHunter being Snake Oil software. If the software is as good as it's author claims it to be, then there wouldn't be such an emphasis put on that support service, and its ability to create custom fixes "just for your computer", which sounds like a bogus claim at best. I later found out reports from users who mentioned trying to call this support helpdesk, only to get no answer or to get rudely hung up upon. Which brings back questions about the legitimacy of the whole thing.
It turns out that ESG seems to be pretty proud of this support service, and don't hesitate to push it a lot publicly, as could be seen in some of Alvin's previously quoted comments, or in this newer advertisement for SpyHunter 4 :
The ad looks actually pretty cool, compared to their previous attempts. But at this point, it'll take more than a low-toned male voice and a snazzy graphical presentation wrapped up into a nifty little video to convince me into trusting this company or their product. The sole idea of one of their technicians taking remote control of my PC to fix a malware infection sends shivers down my spine. The true irony of it all is when I actually noticed (very late might I add, given the amount of stuff I dug out during the course of this investigation) the following article on Enigma's own main webpage, "Beware: Rogue Anti-Virus/Anti-Spyware Programs Offer ‘Real’ Live Chat Support" :
|
Now, tell me, dear reader, how is one supposed to tell Enigma Software Group and its product SpyHunter apart from the "confirmed" rogue anti-malware out there in the wild? Given the marked differences between trusted vendors marketing practices and that of ESG, I would tend to say that this is a very blurry line indeed.
Conclusion
To finish this article properly, I feel the need to remind the reader what is the topic actually discussed here : the manipulation of mass medias through social engineering techniques by unscrupulous marketers (the very same kind of which they want to protect you from) in order for them to gain market exposure and street credibility that couldn't be obtained otherwise. In short, to give them free publicity and a renewed virginity in terms of credibility perception despite its shady past (and one could also add the present). Whether or not ESG is truly a legitimate company or actually fraudulent scammers is beyond the scope of this article. This doesn't change the fact that the company, and its representatives, have a huge credibility deficit, and the reason I focused on ESG throughout this article is because of the media coverage they managed to gain in recent years, being cited as a credible source to the point where news clips about ESG makes it onto security mailing lists without raising any alarm bell, and that despite of this huge credibility deficit that I exposed throughout this paper.
This issue is a serious issue. The press is often being referred to as The Fourth Estate, due to the counter-balance of power the independent press represents in face of the three official branches of the official government. As such, the members of the press have a huge responsibility in front of their readership to double-check their sources and stories before releasing them to the public. Especially in this era of mergers and acquisitions, it is more important than ever for these news media sources to fulfill these responsibilities to their fullest extent, because as the diversity of commercially-independent sources thins out, whatever comes out of the few large media corporations that remains do spread around with a magnified significance as it gets exposed to more and more eyeballs through the various smaller media outlets all belonging to the same corporation.
Unfortunately, the mergers and acquisitions in the media industry are more driven by financial gain and economic considerations rather than the research of truth for greater being of the community. As a result, a phenomenon dubbed "journalistic laziness" has appeared, and which refers not as much as the unwillingness of journalists to properly be motivated to do their job correctly (although in some extreme cases it may actually be the case), but rather to the shortcuts most of them have been forced to do while performing their jobs due to time-constraints and cost-reduction measures, most of them actually induced by the merger spree than began in the early 2000's. One of the best example of symptoms of this "journalistic laziness" phenomenon would be the Jayson Blair scandal (http://en.wikipedia.org/wiki/Jayson_Blair) who managed to get many plagiarized and made-up stories in the pages of the New York Times before finally being caught for it in 2003.
But the issue at hand here isn't one of plagiarism or fake articles written with a fraudulent purpose in mind. The issue is how, in today's fast-paced journalistic environment, the medias collectively failed to make the proper checks on a more than dubious software vendor before granting them space in their columns or on their airwaves, most probably each time making the bet that these checks have been made previously by the authors of earlier articles; and how a software vendor of dubious repute such as Enigma Software Group managed to get a snow-ball effect of mediatic coverage through the means of very simple social engineering tricks : cleaning up of their website of the most misleading parts (like "free scanner" instead of "free removal tool", executable filename properly identifying SpyHunter), a slightly more subtle approach at spamvertising, the public release of a single free tool which removes one single piece of malware (Conficker Removal Tool) and the splattering of their sales data onto a Google Map API, and ultimately giving the news outlets what they want, which is relatively fresh and/or relevant news pieces to fill the blank space/dead air.
Because here lies the main problem I now see with the Malware Tracker Map : notwithstanding how much I like the idea and how useful I think it is to the community, and despite of the most obvious flaw that the data presented is only a small fragment of the reality (which would be the case if any other single vendor would produce a similar web service), now that I know how that data has been gathered and more importantly by who, knowing their past practices and their relatively flexible ethics, I have every reason in the world to start doubting the validity of the numbers presented on this malware tracker map. Is the number a factual number of infections genuinely detected by SpyHunter? Or is it actually a reflection of the downloaded install-base, whether it is paid for or not? Is the detection of cookies counted as "malware infections", and thus also reflected in these numbers? In the light of all that I have covered in this article, these (and possibly more) are all legitimate questions to ask about this malware tracker map.
And if these numbers are unreliable, then all the news articles derived from these numbers around the topic of a demographic study of malware infections by geographical region suddenly become based on nothing else than thin air, which means that the articles themselves are utter bullcrap, presented to the masses as factual truth, as the public is in the right to expect a quality information coming from verified, credible sources, which is the basis of the power of that Fourth Estate that is commonly associated with the press.
Credibility is a valuable commodity, and one that can be quickly lost, and once lost, could be very hard to recover. Journalism and computer security both have in common that they both rely heavily on credibility to effectively manage to perform in their respective lines of businesses. One can understand that a journalist may not have the technical background to judge of the technical expertise of an info-sec specialist, but that still doesn't prevent them from finding out if the source is as reliable and credible as they claim to be. None of the stuff I exposed in this article is technical, but tells a lot about the company's credibility, so the lack of technical expertise on the journalists' side can not be used as an excuse. As soon as I made a few searches on Google, I started digging out interesting stuff. In a matter of approximately 15 minutes, I had over 60 webpages opened on the topic, and of which you just read the collection of my findings through these webpages. I wouldn't have gone through such troubles putting together such an article if what I found during my investigations didn't cry "foul" at me louder and louder as I kept digging deeper and deeper.
Whether or not ESG is now completely legitimate or if they are crooked, the point is that they are not credible in the field of IT security, and by a large margin. The fact remains that they managed, over the last few years, to social-engineer media outlets to the point of gaining enough pseudo-credibility through media exposure that they made it past onto such reputable computer security mailing lists such as ThreatPost. That, in itself, implies that nowadays media outlets are vulnerable now more than ever to be manipulated through the use of social engineering tricks, and deserves the ringing of an alarm bell.
Because if we, the citizens, can't rely on the media to fulfill their role of going after the truth, then it is our whole capacity to make enlightened democratic choices as a society that gets seriously hampered down, and that, is not a good thing, I think.
This issue is a serious issue. The press is often being referred to as The Fourth Estate, due to the counter-balance of power the independent press represents in face of the three official branches of the official government. As such, the members of the press have a huge responsibility in front of their readership to double-check their sources and stories before releasing them to the public. Especially in this era of mergers and acquisitions, it is more important than ever for these news media sources to fulfill these responsibilities to their fullest extent, because as the diversity of commercially-independent sources thins out, whatever comes out of the few large media corporations that remains do spread around with a magnified significance as it gets exposed to more and more eyeballs through the various smaller media outlets all belonging to the same corporation.
Unfortunately, the mergers and acquisitions in the media industry are more driven by financial gain and economic considerations rather than the research of truth for greater being of the community. As a result, a phenomenon dubbed "journalistic laziness" has appeared, and which refers not as much as the unwillingness of journalists to properly be motivated to do their job correctly (although in some extreme cases it may actually be the case), but rather to the shortcuts most of them have been forced to do while performing their jobs due to time-constraints and cost-reduction measures, most of them actually induced by the merger spree than began in the early 2000's. One of the best example of symptoms of this "journalistic laziness" phenomenon would be the Jayson Blair scandal (http://en.wikipedia.org/wiki/Jayson_Blair) who managed to get many plagiarized and made-up stories in the pages of the New York Times before finally being caught for it in 2003.
But the issue at hand here isn't one of plagiarism or fake articles written with a fraudulent purpose in mind. The issue is how, in today's fast-paced journalistic environment, the medias collectively failed to make the proper checks on a more than dubious software vendor before granting them space in their columns or on their airwaves, most probably each time making the bet that these checks have been made previously by the authors of earlier articles; and how a software vendor of dubious repute such as Enigma Software Group managed to get a snow-ball effect of mediatic coverage through the means of very simple social engineering tricks : cleaning up of their website of the most misleading parts (like "free scanner" instead of "free removal tool", executable filename properly identifying SpyHunter), a slightly more subtle approach at spamvertising, the public release of a single free tool which removes one single piece of malware (Conficker Removal Tool) and the splattering of their sales data onto a Google Map API, and ultimately giving the news outlets what they want, which is relatively fresh and/or relevant news pieces to fill the blank space/dead air.
Because here lies the main problem I now see with the Malware Tracker Map : notwithstanding how much I like the idea and how useful I think it is to the community, and despite of the most obvious flaw that the data presented is only a small fragment of the reality (which would be the case if any other single vendor would produce a similar web service), now that I know how that data has been gathered and more importantly by who, knowing their past practices and their relatively flexible ethics, I have every reason in the world to start doubting the validity of the numbers presented on this malware tracker map. Is the number a factual number of infections genuinely detected by SpyHunter? Or is it actually a reflection of the downloaded install-base, whether it is paid for or not? Is the detection of cookies counted as "malware infections", and thus also reflected in these numbers? In the light of all that I have covered in this article, these (and possibly more) are all legitimate questions to ask about this malware tracker map.
And if these numbers are unreliable, then all the news articles derived from these numbers around the topic of a demographic study of malware infections by geographical region suddenly become based on nothing else than thin air, which means that the articles themselves are utter bullcrap, presented to the masses as factual truth, as the public is in the right to expect a quality information coming from verified, credible sources, which is the basis of the power of that Fourth Estate that is commonly associated with the press.
Credibility is a valuable commodity, and one that can be quickly lost, and once lost, could be very hard to recover. Journalism and computer security both have in common that they both rely heavily on credibility to effectively manage to perform in their respective lines of businesses. One can understand that a journalist may not have the technical background to judge of the technical expertise of an info-sec specialist, but that still doesn't prevent them from finding out if the source is as reliable and credible as they claim to be. None of the stuff I exposed in this article is technical, but tells a lot about the company's credibility, so the lack of technical expertise on the journalists' side can not be used as an excuse. As soon as I made a few searches on Google, I started digging out interesting stuff. In a matter of approximately 15 minutes, I had over 60 webpages opened on the topic, and of which you just read the collection of my findings through these webpages. I wouldn't have gone through such troubles putting together such an article if what I found during my investigations didn't cry "foul" at me louder and louder as I kept digging deeper and deeper.
Whether or not ESG is now completely legitimate or if they are crooked, the point is that they are not credible in the field of IT security, and by a large margin. The fact remains that they managed, over the last few years, to social-engineer media outlets to the point of gaining enough pseudo-credibility through media exposure that they made it past onto such reputable computer security mailing lists such as ThreatPost. That, in itself, implies that nowadays media outlets are vulnerable now more than ever to be manipulated through the use of social engineering tricks, and deserves the ringing of an alarm bell.
Because if we, the citizens, can't rely on the media to fulfill their role of going after the truth, then it is our whole capacity to make enlightened democratic choices as a society that gets seriously hampered down, and that, is not a good thing, I think.
Adam Richard
Information Security Consultant






